IT Strategies for Your Business: Worms
Back in 1988, Robert Morris wanted to find out how big the Internet was. He launched about 100 lines of code to find his answer. There were bugs in his code that caused other computers all over the country to become unstable.
The “Morris Worm” affected over 6,000 UNIX computers and caused millions of dollars in damage.
A computer virus does not reproduce on its own. It is a mutating program that adds bad code into applications and usually requires action from the user to spread. A computer worm is completely different.
A worm is a malicious program that replicates itself, automatically spreading through a network. Worms can infect other systems while remaining on the original machine.
Worms take up large amounts of memory, as well as bandwidth. This results in servers, individual systems, and networks getting overloaded.

In this blog, we will discuss some common worm types, how to tell if a computer may have a worm installed on it, and the best ways to protect yourself and your business from worms.
What are the Common Types of Computer Worms?
There are five different types of computer worms: email, IM, IRC, net, and P2P. All these types will attack computers through the Internet in some way.
An email worm is a worm that can copy itself and spread through file attachments in emails. In this case, the worm code will only activate if a file is opened, or a link is clicked. Email worms can be sent if the worm can find the address book in Outlook or Gmail.
An Instant Messenger (IM) worm is a type of worm that can spread through IM chats like Facebook Messenger, WhatsApp, or Skype. When an IM worm is working, it will find the address book that belongs to a user and tries to transmit a copy of itself to all the person’s contacts.

An Internet Relay Chat (IRC) worm will use message boards or forums to spread itself. Like an email worm, an IRC worm will either infect a computer through a link or attachment. The user must accept the file or click the link to activate it.
Net-worms spread through computer networks. These types of worms do not need any action from another person to spread. Net-worms can find new hosts by using shares made over a network. This can be done by using a server or hard drive that a group of computers accesses on a local network.
Peer-to-peer networks are created when two or more computers are connected and share resources without using a server. Peer-to-peer (P2P) worms exploit these P2P connections by sending copies of themselves to users.
How Can I Tell if My Computer Has a Worm?
A computer worm’s main purpose is to use up as many resources as possible. If it can find something to attach itself to, it will soak up all it can and move on to the next resource.
Worms will attack places that can store files, so a good place to start is your local hard drive. If you or your staff notices that files are being deleted, or they are being added, there may be a worm installed.
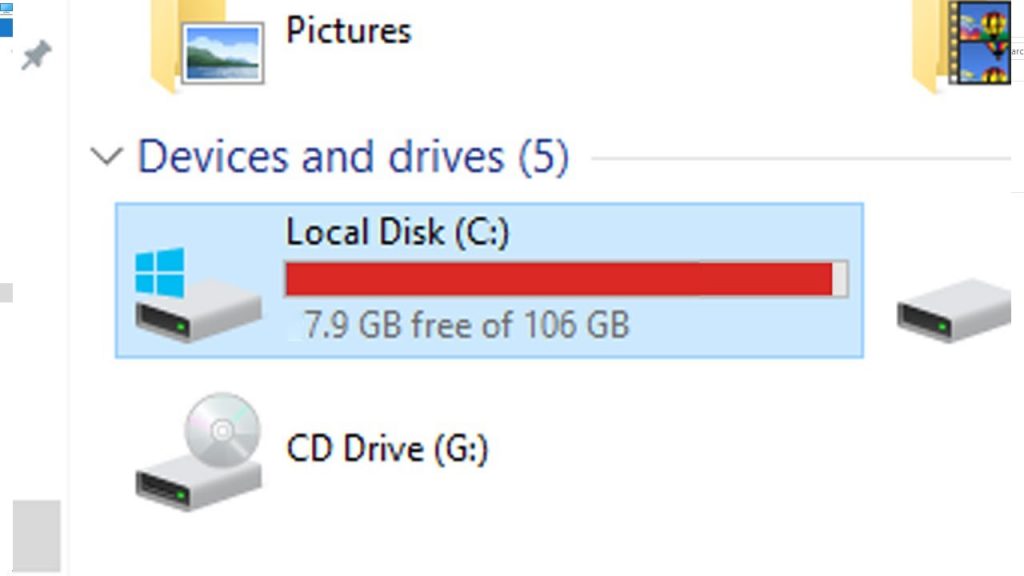
Since computer worms will replicate themselves, they will take up large amounts of hard drive space. If you notice on your computer that your free space is constantly being taken up, it could be due to a worm.
Worms also like to use software to spread themselves. If you or your team notices that their computer is running slowly, or if multiple applications are crashing or running weirdly, it could be because of a worm.
If a worm is sent by email, it will include files with extensions like “.exe,” “.vbs,” “.scr,” and “.bat.” If you or your staff is concerned an email worm may be installed, reach out to your email contacts, and see if they received any files that have those extensions.
How Can I Protect My Computer from Worms?
Computer worms will always look for vulnerabilities, and updates can help protect from those vulnerabilities. Make sure that your staff has the most up-to-date version of Windows or macOS.
If there is any special software you use, make sure you check for recent patches. Manufacturers are always looking for flaws, and they will release patches that address them in system updates.
Worms can be activated through email links and attachments, so make sure you are mindful of phishing attempts. Anytime you or your staff opens an email that you are not expecting, check for suspicious attachments or links. They could contain worms or a command that automatically downloads a worm on your computer.
Your IT team should have anti-virus measures in place to detect intruders on a network. The anti-virus program should also run frequent scans to prevent these attacks from spreading too quickly. If possible, run a full scan every two weeks or once a month.
Windows also has built-in antivirus and threat protection and is a good start if you have not found an antivirus provider yet.
Wrapping Up
Computer worms can attack computers quickly. Whether through email, instant messaging, or directly through a network, it does not take long for a worm to take complete control of a computer.
Most worms can be removed with a solid antivirus program, but it may cause irreversible damage to a computer.
Since nearly all computer worm attacks begin with access to the Internet, you and your staff must practice safe web browsing and other basic precautions when using your computer. Thankfully, the Internet is so massive, you won’t need to do any experimenting like Robert Morris!