
IT Strategies for Your Business: Phishing Pt. 3

Phishing is one of the most common ways hackers gain access to networks and sensitive data. Although it is one of the oldest forms of malicious attacks, hackers still revert to it the most because it is easier to trick the untrained eye.
In previous blogs, we have explained the basics of phishing and detailed some of the common techniques.
In this blog, we will expound on more phishing techniques. We will discuss pharming, clone, evil twin, and watering hole phishing attacks and how to prevent them from affecting your business.
Pharming Attacks
The DNS is the phonebook of the Internet. Your team will access a lot of information online through domain names like google.com or facebook.com. The DNS will translate these websites to IP addresses so browsers can load the page.
Pharming is a phishing technique that is a lot more technical and is difficult to detect. Your IT team will need to be heavily involved to make sure that your business is secure from these attacks.
When hackers use pharming attacks, they hijack a Domain Name Server (DNS). Then, when a staff member types in the website address, the DNS server will redirect the employee to a malicious site that might look real.
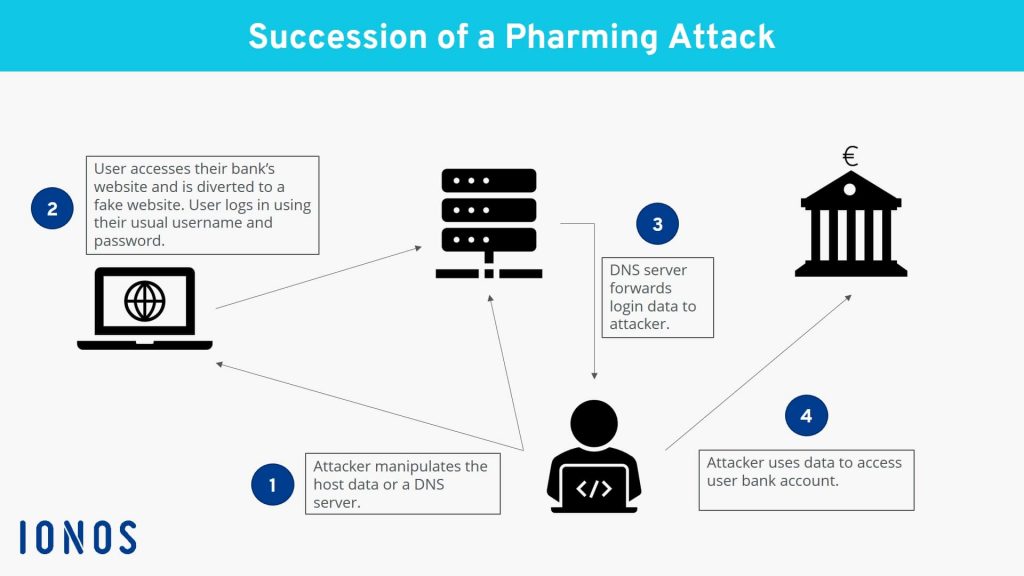
The best way to identify and protect yourself and your team from pharming attacks is to only use websites that begin with HTTPS and not HTTP. Websites that use HTTPS instead of HTTP have higher levels of security that help with data integrity and authentication.
Clone Phishing Attacks
Hackers will attempt a clone phishing attack by targeting users through email. With clone phishing, an attacker will look for services or applications that require staff members to click links as a part of their daily routines.
Hackers will research companies to see what type of programs they use often, and then send emails that appear to come from these programs.
For example, with the work environment shifting to more remote meetings, your staff may receive a lot of Zoom invite links. A hacker would design an email to look exactly like a Zoom invite, hoping the victim will click on it blindly.
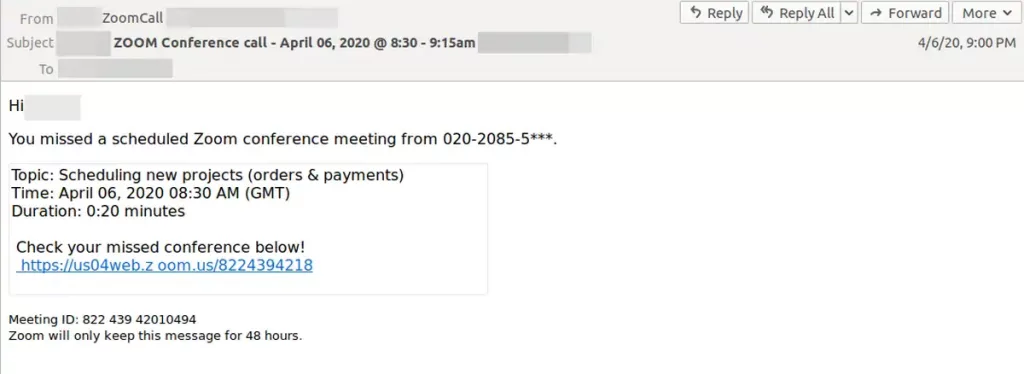
Your team should be mindful of any unexpected email from a service provider, even one that is part of a normal day job function. Usually, these emails will come from an email with a random username or long string of letters and numbers.
You should also be on the lookout for emails that request personal information in applications it does not usually ask for. Going back to the Zoom link example, a passcode to enter the meeting is usually included in the invite and should not be requested!
Evil Twin Phishing Attacks
Cybercriminals also like to trick employees with evil twin phishing attacks. These attacks use a fake Wi-Fi hotspot by making it look legit. If an employee uses the fake hotspot, hackers can begin man-in-the-middle attacks or eavesdropping attacks. Evil twin attacks can help hackers collect sensitive data like passwords or financial records.
With the increasing need for remote work, there are many public places with free Wi-Fi. You and your team should be familiar with the name of the Wi-Fi connection and password if there is one. Hackers like to change the name of Wi-Fi connections, so they look like the real thing.
Pay attention if your computer or phone shows an “unsecured” warning on the screen after you connect to Wi-Fi, even if it looks familiar. You and your team should also have a VPN installed so you can access business data securely.
Also, any Wi-Fi connection that suddenly requires login credentials when it usually does not ask for one is suspicious. Make sure the connection name is correct.
Watering Hole Phishing Attacks
Like clone phishing, watering hole phishing starts with hackers researching the websites a company’s staff visits often. Once they have gathered enough information, they will write the malicious code. Then the hacker will inject the public website with the code; this code is designed to steal personal information.
Cybercriminals like to combine watering hole attacks with zero-day attacks. Since zero-day attacks have no immediate solution, the combination of two attacks makes them very hard to protect against.
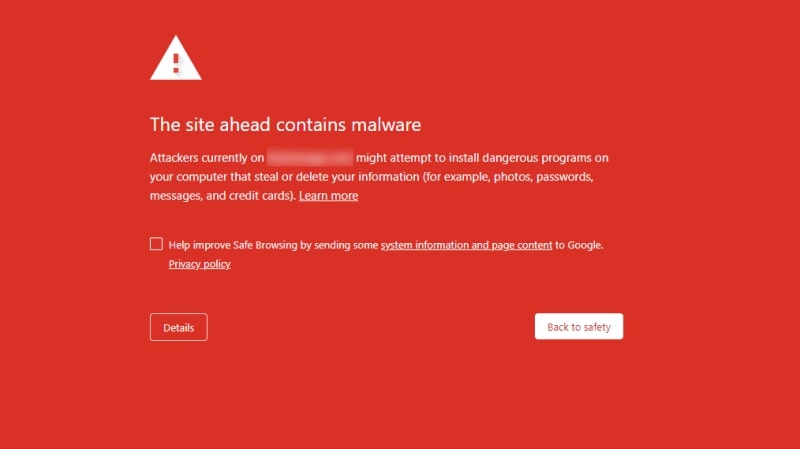
You and your team should pay close attention to browser alerts. Web browsers will tell you if a website has malicious code.
Your IT team should make sure that firewall rules are updated and monitored to prevent inbound traffic from a compromised website.
Wrapping Up
Even though most phishing attacks start with social engineering tactics, newer techniques can be difficult for employees to see. The first and most important line of defense is making sure your team is properly trained on how to protect their information.
Since hackers like to steal login information, it is best to require some form of multi-factor authentication in some cases. The more sensitive the data, the more secure the login should be.
Your IT team can help with email filters to slow down clone phishing. Email filters can scan for additional risks indicating an attempting phishing attack. Finding the right email filtering solution can help reduce the number of risky phishing emails that make it through to employees.

In some cases, it may be best to limit access to the internet. Your IT team can set up access control lists (ACLs). ACLs help create controls for your networks that can deny access to certain websites and web-based applications.
Successful phishing attacks will almost always leave malware or worse – ransomware behind. In a worst-case scenario, some important data might get lost. Your IT team should also have a solid data backup program in place that stores files in multiple locations.




