
IT Strategies for Your Business: Phishing

Did you know that the “Nigerian prince” email scams still make money? A study by ADT calculated that Nigerian letter scams cost users an average of $2,133. Scams like these are so effective to employees because of how easy it is to be tempted.
Phishing is a type of online scam where hackers impersonate legitimate organizations via email, text message, or other means to steal sensitive information. In this blog, we will discuss the different ways hackers will try to trick you or your staff to acquire sensitive information.
Phishing emails may look like they are from a company that is well known or trustworthy. They may look like they are from a bank, a credit card company, a social networking site, an online payment website or app, or an online store.
Phishing emails often tell a story to trick employees into clicking on a link or opening an attachment. They may:
- say they have noticed some suspicious activity or log-in attempts
- claim there is a problem with your account or your payment information
- say you must confirm some personal information
- want you to click on a link to make a payment
- offer a coupon for free items
Here are some ways you and your staff can recognize and protect yourself from a potential phishing attempt:
1. Check the sender.
Who has the email come from? Phishing scams usually try and make the “from” name look like it has come from a legit company. Check the sender address – most of the time the scammer will be using a bunch of random numbers and characters.
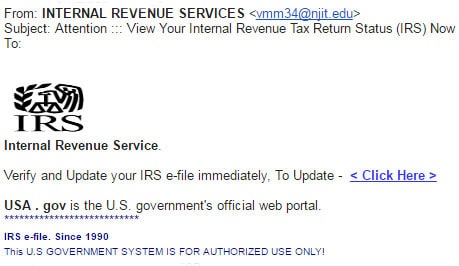
2. How is it written?
A phishing scam will not use personal details such as first and last names. Sometimes spam emails will address others as Mr. and Mrs./Miss or just start as “Hello”.
Also, the phishing attempt may be grammatically incorrect and contain spelling errors. Official emails or texts will be much more formal.
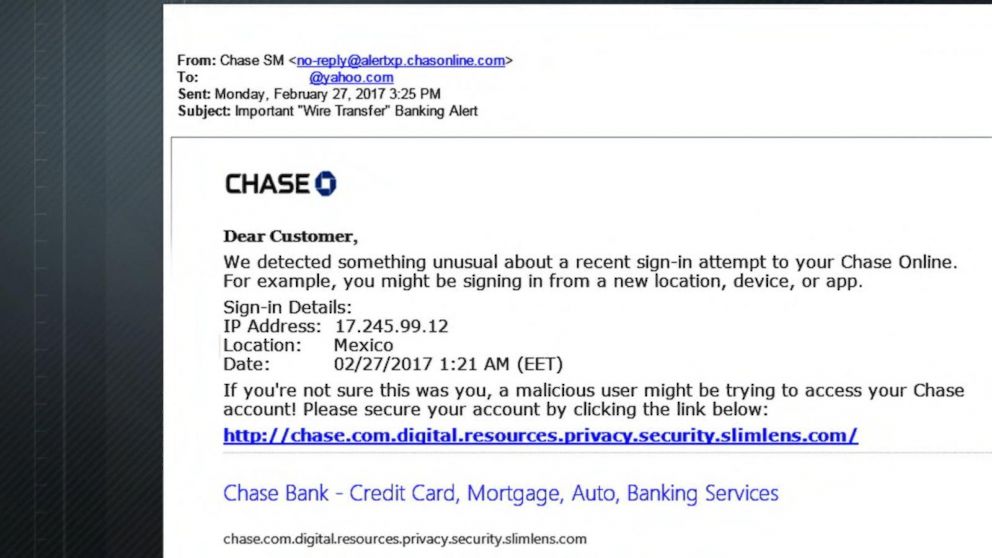
3. Do not click. Use your own link.
If your staff uses a product or service from the company sending them the message, encourage them to not click a direct link. These links will generally come in an HTML format, because HTML files have a lower chance of being detected by antivirus software, and HTML files are not usually associated with email attacks. Secondly, HTML attachments are often used by banks and other financial institutions, so employees are used to seeing them.
Instead of clicking the link directly, they should learn to navigate to the website in another tab. If the email is legitimate, they will see the same information when logging into their account.
For example, if a staff member receives an email from Chase saying there is some unusual activity on their account, they should log onto chase.com and see if that same notification is there.
4. Stay updated.
Please be sure to confirm with your IT department about setting antivirus software on staff machines to update and run periodic scans so it can deal with any new security threats.
Also, have your staff check for smartphone updates. These updates could give critical protection against security threats.
Sometimes a common phishing scam is for a hacker to send an email to upgrade their account or authenticate their account. The link will include a direct link to complete this “update”. Your staff should be informed on how to properly upgrade their machines or reset their password. If possible, your IT team should create documentation or schedule training days to educate your staff on best practices.
5. Use multifactor authentication.
Some email accounts offer extra security by requiring two or more credentials to log in to an account. This is called multi-factor authentication. The additional credentials needed to log in to an account fall into two categories:
- Something you have — a passcode obtained via text message or an authentication app.
- Something you are — a scan of a fingerprint, eyes, or facial recognition.
Multi-factor authentication makes it harder for scammers to log in to accounts if they happen to get access to an employee’s username and password.
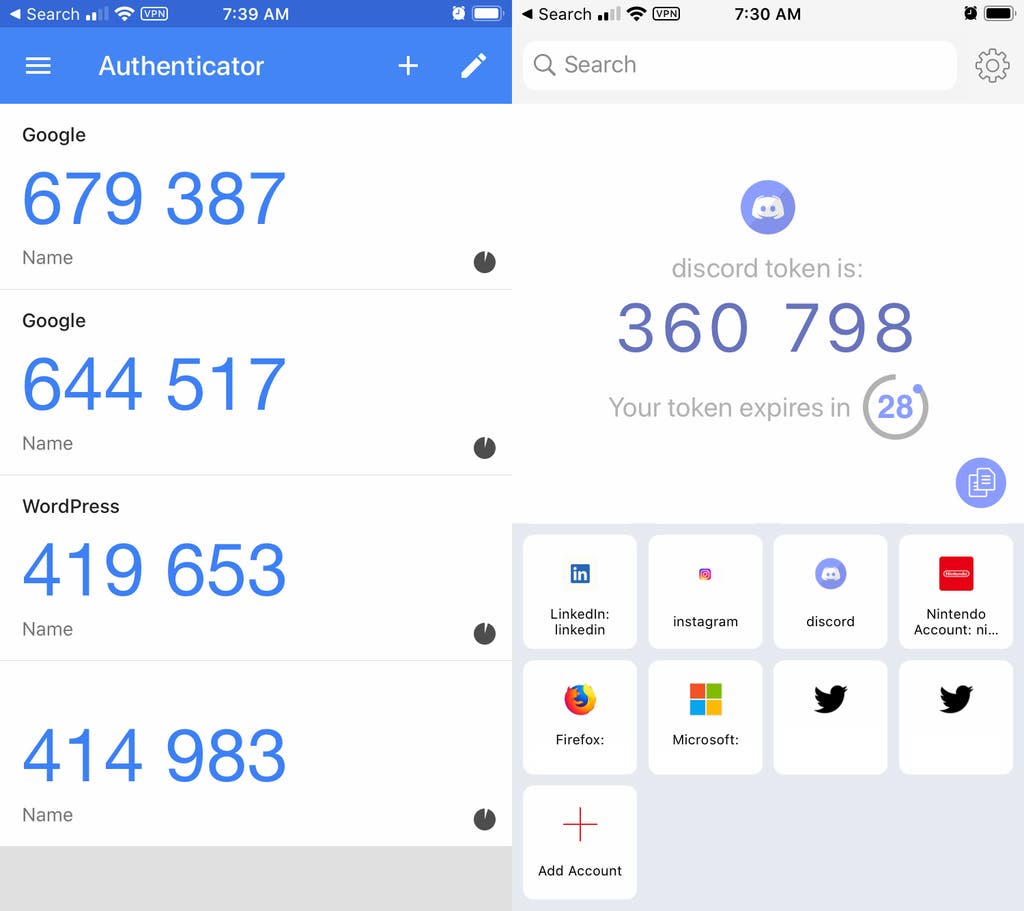
Please note that it is not recommended to use a text message as a form of multifactor authentication, text messages are less secure than apps like Google Authenticator or Authy. For example, hackers have been able to trick people into porting numbers to a new device with a maneuver called “SIM swap”. Once a hacker has redirected your staff’s phone number, they will no longer need your physical phone to gain access to their multifactor authentication codes.
In conclusion, phishing is one of the more common ways businesses can be coerced into giving away sensitive information. You must convey to your staff the easy ways hackers try to steal information. Furthermore, it is also imperative that your IT team has solid web filters in place, and that the email client you use can efficiently filter out spam email addresses from cluttering your employees’ inbox.





Comments are closed.