
IT Strategies for Your Business: DDoS Attacks

In September 2017, Google got hacked. Google’s cybersecurity team discovered that a hacker in China used several internet service providers (ISPs) to attack thousands of Google IP addresses. This attack on Google’s network lasted for six months. The attacker transferred 167 Mpps (millions of packets per second) of data with what is known as a distributed denial of service (DDoS) attack.
Of course, Google was able to get back up and running in no time, but for a lot of small businesses, DDoS attacks can be costly. IT security professionals have estimated that DDoS attacks can cost up to $50,000 per attack.
A DDoS attack is a malicious attempt to disrupt the normal flow of a network by overwhelming the target with a flood of internet traffic.
In this blog, we will discuss how DDoS attacks work, three common types of DDoS attacks, how to identify them, and some steps you and your IT team can take to prevent them from hurting your business.
How does a DDoS attack work?
A DDoS attack is like an unexpected traffic jam that clogs up the highway, preventing regular traffic from getting where it needs to go.
DDoS attacks are so effective because they can use multiple machines as a source of internet traffic; practically anything with Wi-Fi access can be used to initiate a DDoS attack.
Once the hacker has chosen the group of devices needed, the hacker will then infect them all with malware, allowing them to be controlled remotely. These individual machines are referred to as bots or zombies. The collective group of hacked machines is called a botnet.
Lastly, once the hacker has established the botnet, each bot will be given a set of instructions. In these instructions, each bot is ordered to send a request to a target IP address. With the mass number of requests being sent to the target, the DDoS attack is complete.
Common Types of DDoS Attacks
The impact of a DDoS attack can range from a minor annoyance from disrupted services to experiencing entire websites, applications, or even entire networks being taken offline.
There are three primary types of DDoS attacks: volume-based, network-layer, and application layer.
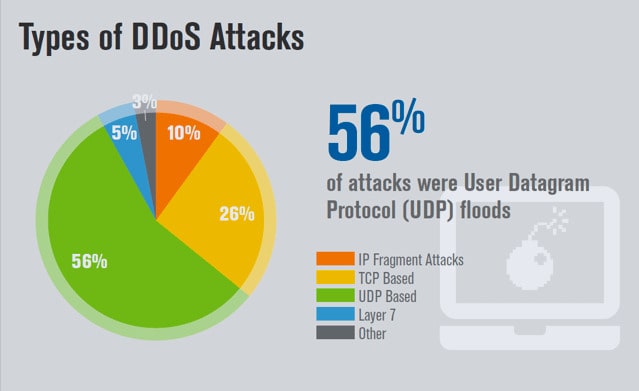
Volume-based attacks use large amounts of traffic to overwhelm a target such as a website or a server. The goal of this DDoS attempt is to create congestion by consuming all available bandwidth between the target and the Internet.
Network-layer attacks send large numbers of packets to specific networks and network management tools. The attacks will overwhelm network management tools like firewalls or web filters.
Application-layer attacks are DDoS attacks conducted by flooding applications or websites with requests. The botnet will target where web pages are generated on a server and delivered.
How to Identify and Stop DDoS Attacks
With DDoS attacks, your team may notice that they have slow access to files, either locally or remotely.
They may have a long-term inability to access a website or accessing any websites. Employees could receive a mass amount of spam emails, or they could have internet connectivity issues.
These are not unusual issues, and if they happen individually, it is most likely unrelated to a DDoS attack. The issue may be isolated to one staff member or service. However, if a wide range of users experiences two or more of these symptoms for a long period of time, your team might be victims of DDoS.
Password strength is crucial; hackers love to make bots out of machines with weak passwords. It is also important that every machine on your office network is updated regularly. Windows and macOS updates generally push out security patches that can help slow down these attacks.
Because these symptoms are common with most computers, detecting DDoS attacks can be difficult without the proper tools. Your IT team should have proper networking tools in place to detect unusual data transfers.
Ideally, your IT team will need to make sure that firewalls and routers are set up to reject bogus traffic. Network tools also need to be updated with the latest security patches. Your business’ firewall and router configuration will be your first line of defense from these attacks!
Also, it is important that your IT team separate employee network traffic from software-generated traffic used in DDoS attacks. This can be done using IP address filtering or by blacklisting and whitelisting traffic.
Wrapping Up
In conclusion, DDoS attacks are different from other hacking attempts because they do not introduce malware in networks or services used by a business. Instead, hackers using DDoS basically hold important services hostage until businesses stop it or are willing to pay up, in some cases. These attacks are becoming more complex and more frequent, targeting any business regardless of size. You and your staff must understand how any device can be used against them if not properly secured. Your staff should know the importance of strong passwords and device updates.
Lastly, your network infrastructure should have tools to deal with common DDoS attacks, and your IT team must have a solid network security backbone in place to help keep your business secure.





come dimagrire velocemente
come perdere la pancia
“Next time I read a blog, Hopefully it won’t disappoint me as much as this one. After all, I know it was my choice to read, but I really believed you’d have something helpful to talk about. All I hear is a bunch of moaning about something you could fix if you weren’t too busy looking for attention.”
“Good post. I learn something totally new and challenging on sites I stumbleupon everyday. It’s always useful to read content from other writers and use something from other sites.”
“I was extremely pleased to find this web site. I need to to thank you for your time due to this fantastic read!! I definitely enjoyed every part of it and i also have you saved to fav to see new stuff in your website.”
“Hi there! I simply would like to give you a big thumbs up for the excellent information you have got here on this post. I’ll be returning to your site for more soon.”
“Everything is very open with a really clear description of the issues. It was truly informative. Your website is extremely helpful. Many thanks for sharing!”
Comments are closed.